Information security is an evolving challenge. This responsibility is shared by all UM employees, students, vendors, and everyone else who contributes to our academic community.
Information security is an evolving challenge. This responsibility is shared by all UM employees, students, vendors, and everyone else who contributes to our academic community.
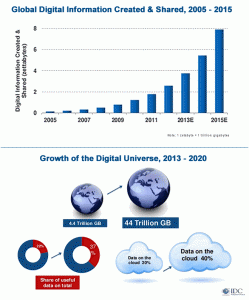
Consider for a moment the illustration shown on the explosion of digital information. This exponential growth is being driven by an increasing number of intelligent connected devices. Inevitably, this trend will also continue making it more challenging to keep tabs on what private information may be exposed.
Digital information will become one of our most valuable assets and we must secure it using a good baseline of protection. This can be challenging with a limited budget and resources. However, our primary focus needs to initially be just on what exposes us to the most risk, our sensitive data.
What is Sensitive Data?
Sensitive data is our most confidential information. It is Personally Identifiable Information (PII), which can be used to distinguish or trace an individual. It is regulated by law, and requires UM to report to the government, and/or provide notice to affected individuals, if records are inappropriately accessed.
In particular, sensitive data includes: An individual’s First Name, or First Initial and Last Name, in combination with any one or more of these elements:
- Social Security Numbers
- Driver’s License Numbers
- State Identification Card Numbers
- Military ID Numbers
- Passport ID Numbers
- Physical, Mental, or Medical Health Records
- Health Insurance Policy Numbers
- Financial Account Numbers (checking credit debit) combined with an Access Code or Password
Guidelines on Protecting Sensitive Data
UM provides guidance on this topic through the Information Confidentiality / Security policy, the Storage Platform Guide, and additional resources on the IT Security website. Here are a few highlights to keep in mind:
- Only use approved storage, transport, and sharing methods:
- Sensitive data should NOT be collected via unauthorized Web Forms, stored on Mobile Devices, Removable Media, or sent through Email, unless it is encrypted. Many Cloud services are also restricted.
- Identify and change internal processes which use sensitive data:
- Review procedures often to ensure compliance. Discover where data lives, who has access, and how it is used. Destroy or anonymize unneeded data.
- Encrypt sensitive data which must be retained:
- Ensure data remains safe and legal even if accessed by malicious actors. Encrypt all Files, Removable Storage, and Portable or Mobile Devices with sensitive data.
Summary of Responsibilities
The University of Mississippi is committed to securing the confidential information critical to its core missions, and to protecting the privacy of its faculty, staff, and students. This resiliency can be achieved by working together as a team and becoming more aware of the security concerns regarding sensitive data.
Departments are ultimately responsible for ensuring the security and integrity of their own computers and data. The Office of Information Technology is here to help assist in any way possible. Please contact us with any questions or concerns.
NOTE: This article is not meant to cover the full scope of FERPA and other federal compliance regulations.
Tags: infosec, IT Security, UM Information Security